As businesses grow their digital footprint, the threat of cyberattacks rises with it. Small businesses are particularly vulnerable, as many simply don’t have the budget or expertise to protect themselves.
A recent survey found that small businesses account for nearly half of the data breaches occurring in the United States, while 61% of small to medium businesses have experienced a cyber-attack in the last 12 months.
The problems caused by cyber threats continue to increase. Many colleges and universities now offering programs specifically in cybersecurity to help meet the need for experts in this field including West Virginia University and Fairmont State University.
But, in the meantime, what can businesses do to keep data safe? We’re sharing our top cybersecurity tips that you can start implementing in your small business straight away.
What Cybersecurity Threats Does Your Business Face?
Before we take a look at some cybersecurity tips for small businesses, it’s important to understand the types of threats that your business may be up against.
Malware is often the biggest threat to a business of any size. Spyware, viruses, or computer “bugs” can easily be installed on a network and spread malicious code throughout your IT system. Once there, the malware can read your most sensitive data and files, and even stop you from being able to access that information yourself.
Phishing attacks are also prevalent in the business world. This is where hackers or scammers try to access your data via emails and links that look as if they’re genuine. Because these sources look legitimate, users will often click on them and malware is installed on their computer as a result of this.
Phishing can also happen when users are lured into sharing personal details, like login information, with scammers via social networks or text. These kinds of password attacks are very common and can even happen when a scammer is able to guess the login details that you’re using. That’s why having secure passwords is a crucial part of having good cybersecurity.

Ways To Protect Your Business From Cybersecurity Threats
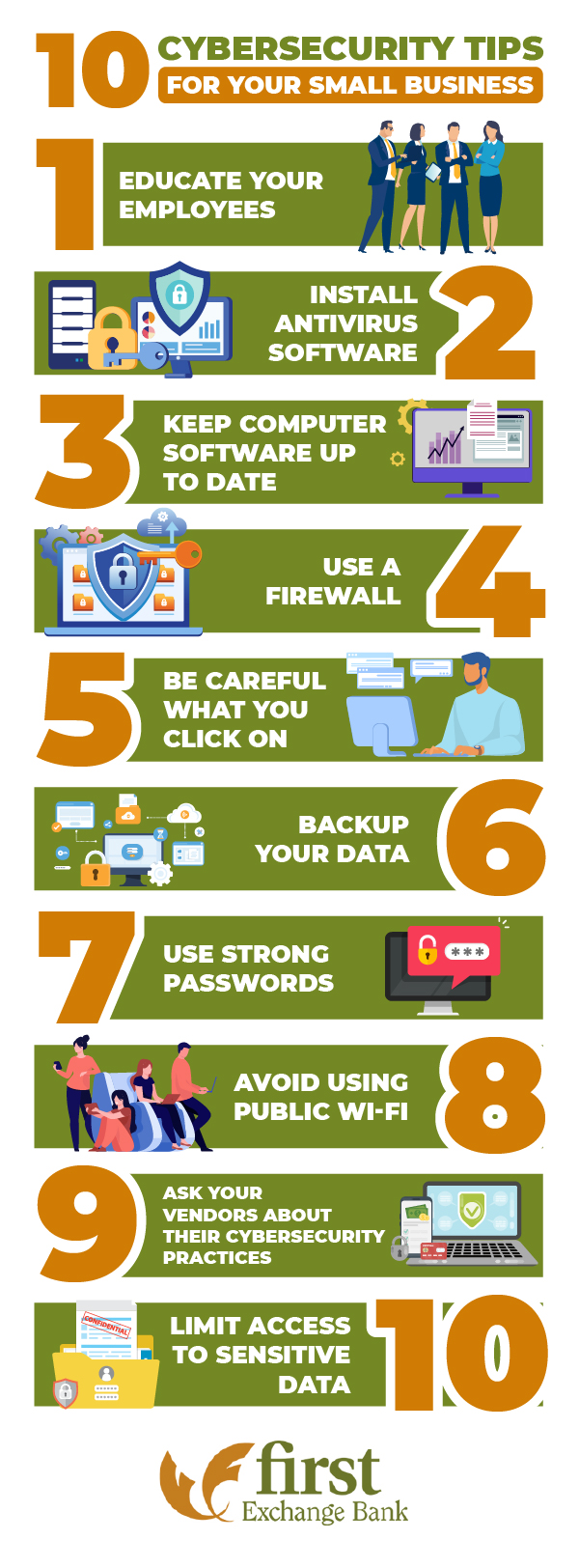
1. Educate Your Employees
Your first line of defense against cyber threats should always be educating your team members. Since phishing can target anyone, particularly those employees with a business email address, it’s vital that they’re aware of what to look out for and how to report any suspicious activity.
All staff should be provided with regular training to keep their skills up-to-date and give you the opportunity to share new threats that they should be aware of.
Any team members with access to sensitive customer data should be given additional training that’s relevant to their role on how to protect this information. Scammers will often use this information to commit identity theft, so it’s vital that everyone with access to these details are fully informed about possible threats and how to avoid them.
2. Install Antivirus Software
Every piece of technology that’s used within your business should have antivirus software installed. This regularly scans your devices and network for malware and provides a layer of protection against potential cyber threats.
After you make any large-scale updates to your devices, you should always run a full scan through your antivirus software to ensure that – nothing malicious has been installed during that update.
3. Keep Computer Software Up To Date
You shouldn’t only rely on your antivirus software to keep you protected. Any devices and software that you use in your small business should be running on the most recent version. That includes operating systems, web browsers, or any apps that you use.
Software companies release updates frequently that include important upgrades like bug patches or enhanced security features. If you’re still using an older version, you won’t be benefiting from the additional protections that the software’s teams have developed.
4. Use A Firewall
Firewalls should be installed as a secondary layer of defense after your antivirus software. While antivirus software scans for existing malicious code and can help to prevent new issues, a firewall is a much stronger software that provides protection between your internal networks and external networks, like the web.
With a firewall, you can block access to certain websites on a company-wide scale or add exceptions for anything that may be needed for your team to carry out their job duties. You should frequently review the settings that you have enabled on your firewall to ensure that you’re adequately protected.
5. Be Careful What You Click On
Malware is often installed on company computers through targeted phishing attacks on employees. In most cases, this is via an email or message that appears to be from a legitimate source, like the government or shopping sites like Amazon. In reality, these emails are sent by scammers with links that install malware once clicked on.
Any cybersecurity training that you provide for your team should include information about this type of threat. Employees must be aware of what to look for in a phishing email and how to identify if clickable links are genuine or scams.
6. Backup Your Data
No one expects the worst to happen. But more than a third of small businesses have experienced critical data loss as a result of a cyberattack. That’s important information that you can’t get back and may open up your team and customers to a confidential data breach.
That’s why it’s so important to create backups of your files and data, and to save these on a separate network to the one that you’re using everyday. Systems and files should be backed up on at least a weekly basis. Setting up programs to do this automatically can save you time and, ultimately, money if your devices are attacked.
7. Use Strong Passwords
Implement a policy across your business to ensure that all passwords are updated at least once per quarter and set minimum requirements to help prevent scammers from guessing any employee passwords that may be in place.
Multi-factor authentication is also another great way to protect login details. This is where additional information is needed for someone to login to an account–a code is usually sent to a mobile device that the user will need to input in order to complete the login.
8. Avoid Using Public Wi-Fi
Public Wi-Fi is notoriously unsecure, so it’s best to avoid using this wherever possible. Sticking to secure, hidden, or even encrypted networks can help to prevent anyone from outside your business accessing your computer via the Wi-Fi network.
If you’re not able to avoid public Wi-Fi at certain times, you should make use of a VPN system. These allow you to stay anonymous while you’re online and hide your location and private data from anyone else on that Wi-Fi network. While they can’t prevent you from downloading malware, VPNs can protect your business from web-based attacks.
9. Ask Your Vendors About Their Cybersecurity Practices
If you’re working with vendors outside of your business like banks or customer relationship manager (CRM) firms, you should always find out what their cyber security practices are.
For anyone handling your sensitive files and information, there should be clearly outlined guidelines and procedures in place that cover how they protect your data from being accessed and what measures would take place should a cyberattack happen.
10. Limit Access To Sensitive Data
Accidentally installing malware or providing access to confidential information is much easier to avoid when you have practices in place that limit which members of the team deal with this information to begin with.
Set up access on an individual basis for any critical files or customer data to ensure that no unauthorized people can see this information. Admin rights should be allocated to a select few within the business and these employees should be trained on cybersecurity threats more frequently.
Develop A Cybersecurity Response Plan
Having a dedicated cybersecurity plan in place can help you to act quickly and efficiently in the event that a security breach does occur. This document should be created in collaboration with your IT team and any cybersecurity professionals that you may be working with.
There are generally four phases that should be covered in a response plan, including:
- Preparation
- Detection and analysis
- Containment, eradication and recovery
- Post-incident response
The plan should outline all of the employees and any external vendors who are the points of contact for a cyberattack, along with what their roles are in the event of a security threat. All incident prevention measures should be listed in the plan (that’s things like the antivirus or firewall software you’re using, scheduled training etc.), along with details about how any attacks are detected.
From there, your plan should also note what information you’ll need to record if an attack takes place. This could include the potential damage and outcomes, what type of resources will be needed to contain the threat, and how effective any solutions might be. You’ll also need to include information about who needs to be notified during or immediately after an attack. If your customer data has been breached, it’s up to you to let them know and what you’re doing to fix the situation.
You should also report any cyberattacks to the government via the FBI cyber investigation site or the Cybersecurity and Infrastructure Security Agency (CISA). Their experts can help support you as you recover from a cyber threat and provide guidance on protecting your small business in the future.